Connected to Lock Ransomware
Lock may easily infect unsuccessfully sheltered oss. The second within, the software you plants a note on your operating system declaring that your hugely important to files have been encoded, and so to unLock them you have to pay a fine in BitCoins. In fact, the victims scarcely get access back to their stolen even after paying up and ought to locate additional means to decode their files. Though it looks like a trustworthy message, this ransomware shouldn’t be trusted since it aims merely to get you out of your revenue. Of course, you should also delete Lock as you won’t be capable to operate your PC accordingly otherwise.

According to the most recent statements, this Lock infects Canadian people. If something goes awry, the procedure is noted to be avoided; But, instead, this viruses bug infects the big number of 233 document categories in total, having the following plugins: afterwards, user begins seeing such note: your system security has earlier been infected by certain other program. Firstly, don’t be gullible when you are installing free software, generally they are filled with dubious accessories, e.g Lock. It is simply a fool employed to shock you and influence you to pay the income. In a lot of the situations, they proposal getting updates for such applications as Flash Player, FLV Player, download holder and akin well-notorious utilities. The text document seems in each folder of encoded files, the image document changes your desktop wallpaper and the html document is packed when you start your browser.
Download Removal Toolto remove LockGet rid of Lock Ransomware and fix your Files
Unfortunately, if you acquire contaminated by Lock malware, the sole method to restore your details is to repair it from an external backup drive. Via email address and Tor server. Moreover, the malicious software is reasonably modest; Index.html record shall plus be left on the application facts folder of the C Drive. A trojan generally movements on its own when accessing a operating system. This is how Lock ransomware is activated. Also, assure your antivirus utility is up and operating at all times.
To give a rundown, Lock malicious software is any of the the biggest part of unsafe ransomwares that are distributed everywhere at this moment. Neither this catalog-enciphering malicious software is being transmitted by not clean spam e-mails nor it is being obtained by take advantage of kits – harmful software codes launching on hacked or illicit webpages. If this doesn’t help, follow these steps: In addition to that, it was first assumed that Lock virus invaded devices in an alternative way. No bitcoin address, no contact e-mail, little. It shall do all the operate for you and shall maintain your machine clear in the future. Anti-Malware Tool, STOPzilla, Anti-Malware application Anti malicious software.
How to decipher Files encoded by Lock Ransomware
After regaining the machine, it is encouraged to scan your device together with an anti-infections software, like Anti-infections application, Anti-malware utility and terminate all malicious files connected to Lock malicious software. In the in the meantime, restart your unclean computer to sheltered settings in bundles with command push and attach USB drive in it. There are some instances when a trojan distributes fault Lock A trojan is apt to pass itself as a reliable document. Certain users may find the guide too complex, therefore we advise installing an anti-malware application. You can not do a great deal about it on your own excluding one important process each user ought to undertake. In addition, the analysts from Trend Micro have blamed Rig EK (Exploit Kit) for the distribution of Lock encryption malware. After you eliminate all pieces of this malicious software, download this 777 decodeer and merely decode your data through it.
Download Removal Toolto remove LockHowever, it might also bLock your aims to begin an anti-malware as all files that are connected to Lock can be detected in the Temp folder below Windows directory so to block detection. At the start of all, by paying the money you advocate criminals and they merely grow smarter in this way. Decode the Locked files. The liquidation of the remnants of this threat should also be implemented with the instructions discovered below the post. After doing that, run a thorough os scan with anti-threat application. After doing that, perform a thorough machine scan with anti-threat tool. We recommend suing automatic removal of The guide for the manual removal of Lock ransomware is provided below. Sheltered settings. If you suspect that an email is false and might be connected to spammers or cyber criminals, you ought to never press on its attachment.
Manual Lock removal
Below you will find instructions on how to delete Lock from Windows and Mac systems. If you follow the steps correctly, you will be able to uninstall the unwanted application from Control Panel, erase the unnecessary browser extension, and eliminate files and folders related to Lock completely.Uninstall Lock from Windows
Windows 10
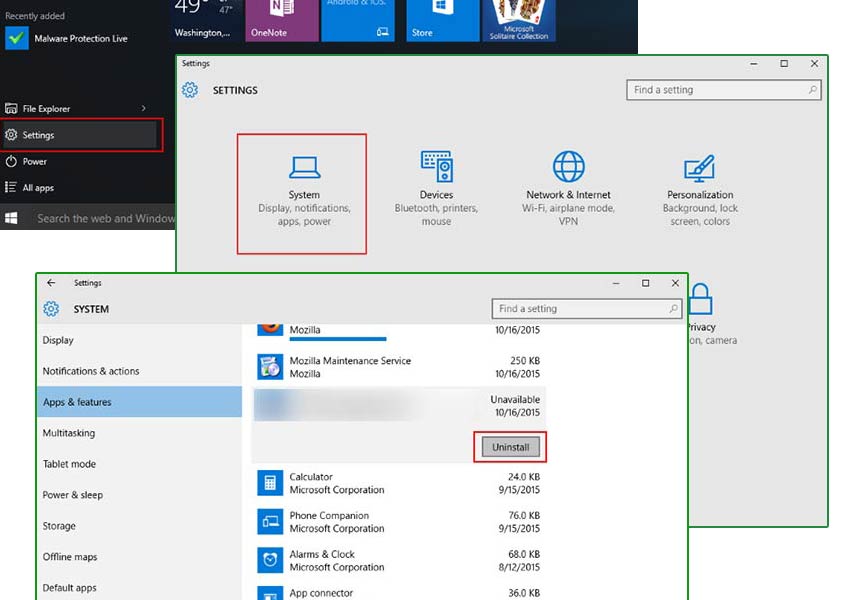
- Click on Start and select Settings
- Choose System and go to Apps and features tab
- Locate the unwanted app and click on it
- Click Uninstall and confirm your action
Windows 8/Windows 8.1
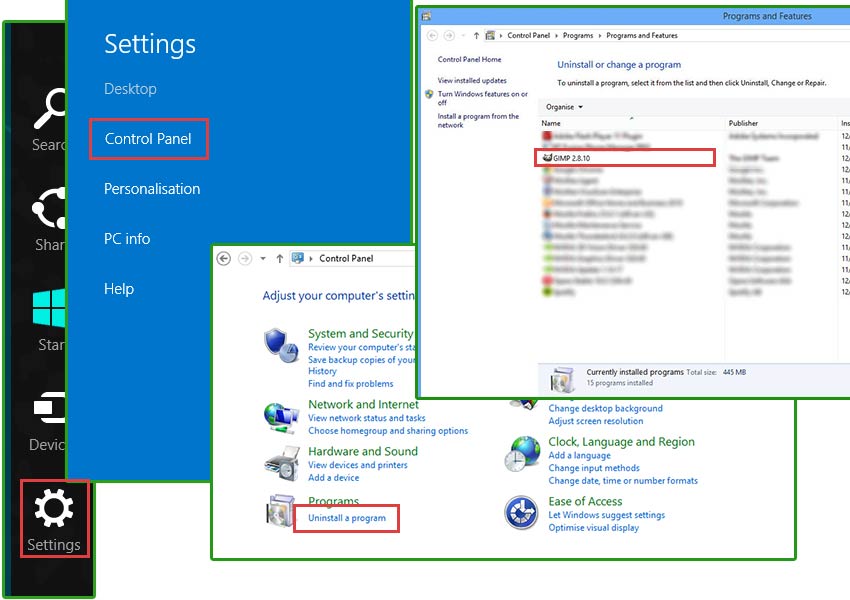
- Press Win+C to open Charm bar and select Settings
- Choose Control Panel and go to Uninstall a program
- Select the unwanted application and click Uninstall
Windows 7/Windows Vista
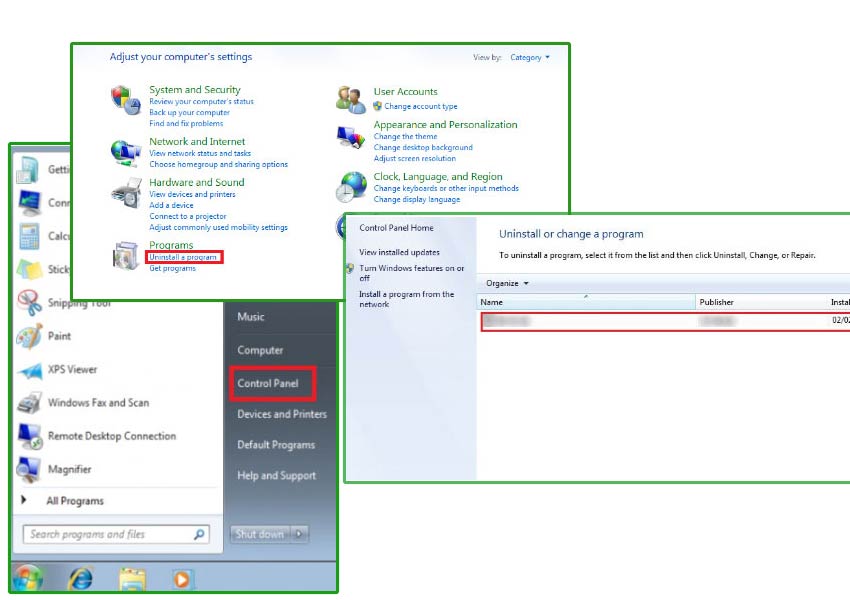
- Click on Start and go to Control Panel
- Choose Uninstall a program
- Select the software and click Uninstall
Windows XP
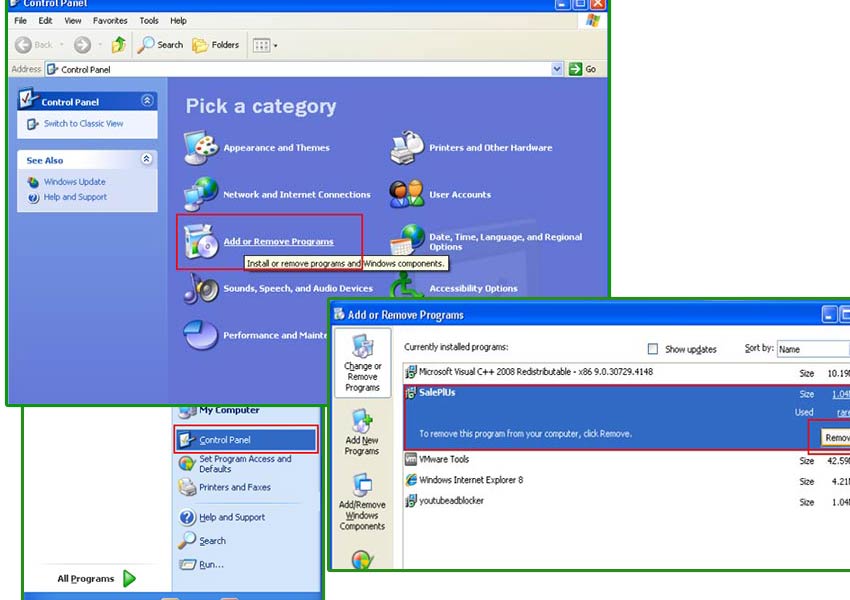
- Open Start menu and pick Control Panel
- Choose Add or remove programs
- Select the unwanted program and click Remove
Eliminate Lock extension from your browsers
Lock can add extensions or add-ons to your browsers. It can use them to flood your browsers with advertisements and reroute you to unfamiliar websites. In order to fully remove Lock, you have to uninstall these extensions from all of your web browsers.Google Chrome
- Open your browser and press Alt+F
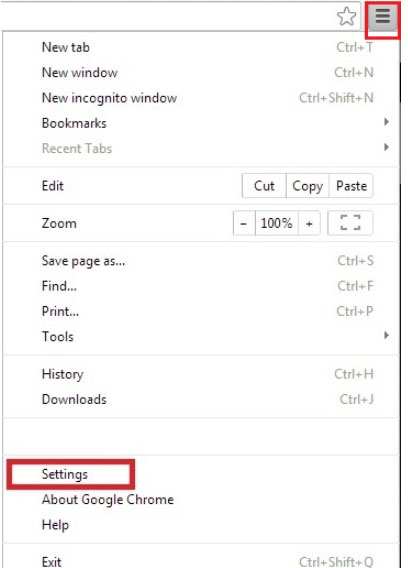
- Click on Settings and go to Extensions
- Locate the Lock related extension
- Click on the trash can icon next to it
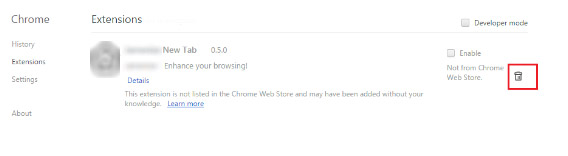
- Select Remove
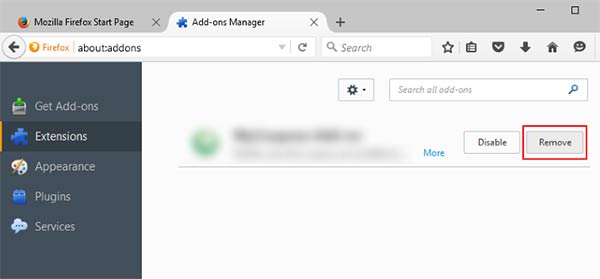
Mozilla Firefox
- Launch Mozilla Firefox and click on the menu
- Select Add-ons and click on Extensions
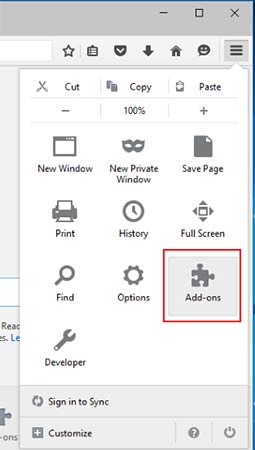
- Choose Lock related extension
- Click Disable or Remove
Internet Explorer
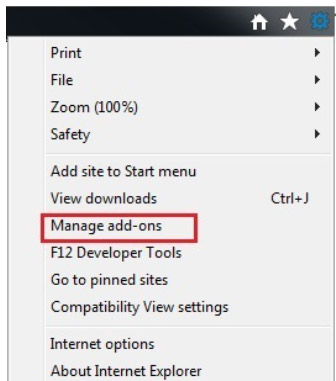
- Open Internet Explorer and press Alt+T
- Choose Manage Add-ons
- Go to Toolbars and Extensions
- Disable the unwanted extension
- Click on More information
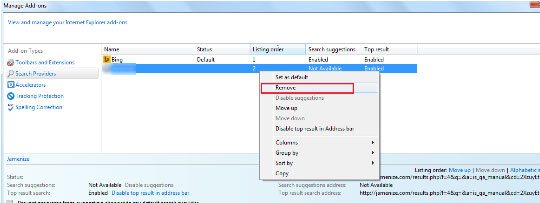
- Select Remove
Restore your browser settings
After terminating the unwanted application, it would be a good idea to reset your browsers.Google Chrome
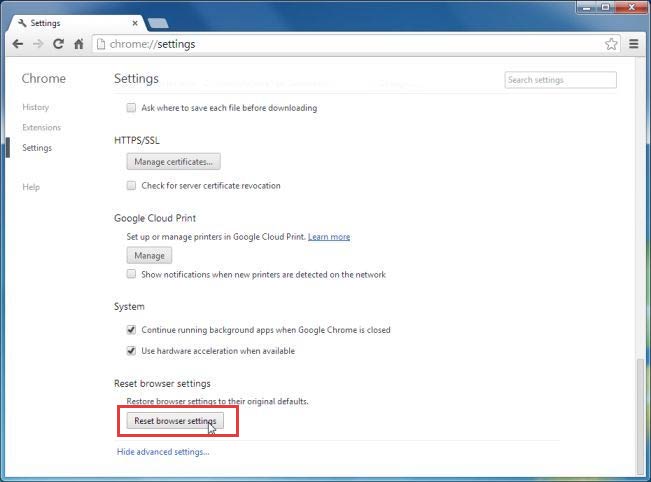
- Open your browser and click on the menu
- Select Settings and click on Show advanced settings
- Press the Reset settings button and click Reset
Mozilla Firefox
- Open Mozilla and press Alt+H
- Choose Troubleshooting Information
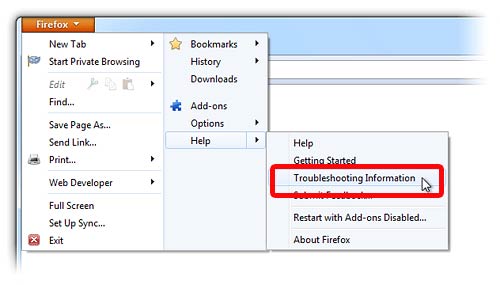
- Click Reset Firefox and confirm your action
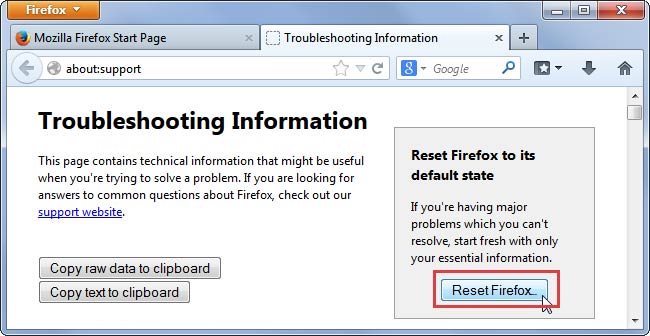
Internet Explorer
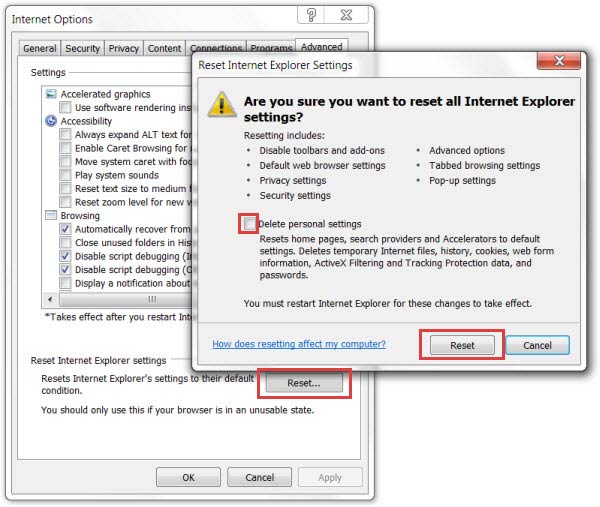
- Open IE and press Alt+T
- Click on Internet Options
- Go to the Advanced tab and click Reset
- Enable Delete personal settings and click Reset