Related to RedProtection
‘Your RedProtection are encrypted’ (must also be detected as ‘Your RedProtection are encoded by CTB-Locker’) is a false notice notification, which belongs to CTB Locker RedProtection This cyber risks is an alarming ransomware utility, which starts different trouble for users. It is the at the start entirely usable ransomware that influences OS X platform. For now, we shall do our greatest to introduce you together with the data which are earlier produced notorious related to this ransomware malware. That’s why you ought to your system with good anti-malware software. Basically, it reveals you to pay 100 euros via Ukash or Paysafecard payment operating systems. Try to avert its drawn-out nails and wake up from a interrupting dream that this issue highly is.

RedProtection is circulated through well-notorious methods that must be kept in mind indefinitely. However, the matter is, it isn’t a resolution. Then this malware leaves penalty notices on the desktop and in each folder that carries the enchiphered numbers; As a resolution, malicious software locks down the os and begins displaying its bogus warning that statements relating to created internet crimes. In addition, as a result developing it glimpse dependable. Nonetheless, you should beware when receiving email notifications from not known senders and appear vigilantly for controversial signals, which are moreover offer in these circumstances.
Download Removal Toolto remove RedProtectionHow are Ransomware infections travel?
Ransomwares and other nasty pc malware are apt to abuse safety gaps, use abuse kits, Trojans, false pop-ups and other complicated things to get into the operating systems. The contact e-mail provided is centrumfr@india.com Besides, it’s highly recommended to follow safe browsing rules and avoid suspiciously-looking websites and messages that reach on social networks. So, since you may see this new ransomware infection has undeniably got errors. For that, we don’t advise termination in a manual way you don’t have plenty of understanding about computers and operating system architecture. Sadly, this may not aid you to obtain your files back; Delete it and do the same thing with the registry key that enables RedProtection ransomware every time you turn on your PC.
You need to take ransomware malicious software greatly, as if such malware got into the device and encodes all files on it, you can’t decode your files anyhow except from a backup. You can safeguard your operating system from threat with a dependable malware removal tool software; Anti-threat utility or Hitman. the good news is, there are a certain number of programs that might be employed for unlocking enchiphered files. A lot of of these risks distributed as attachments to laughable email letters. Frequently, spam emails include typing or grammar errors. This quiz is, basically, the instructions on the course of actions to be taken by the affected user from the perspective of the coder/coders of RedProtection ransomware.
How to decipher Files enchiphered by RedProtection Ransomware?
The hotbed for infections like RedProtection virus is email accounts. So to paralyze the Flash, go to Macromedia advocate and favor ‘Deny': at the current moment, the malicious software chooses to get into computers via slither ontoed spam emails. The bad news is that a lot of ransomware viruses use advanced and critical crypto-algorithms to enchipher victim’s statistics, and in most situations, such algorithms are not possible to hole. Criminals even mimic from infamous commercial businesses so to sound more dependable. In addition, he said that he earned profitable data interacting with other crooks as via Tox dark net which is accessible via anonymous Tor browser. It will prevent infiltration of dangerous/potentially not wanted software and keep your machine’s protection. Finally, after the RedProtection is eliminated, ensure you back up extremely important to files.
Download Removal Toolto remove RedProtection* They store copies of your files that fact of time if the machine recover snapshot was invented. So to freeze the Flash, go to Macromedia advocate and opt for ‘Deny': Anti-parasite Tool, Anti-parasite application or Anti-parasite Tool. After doing that, execute a full device scan with anti-viruses software. ’’, when the user aims to launch any of the oriented files. You shall advise con artists to go on their motions and intended etc. malicious software like
Manual RedProtection removal
Below you will find instructions on how to delete RedProtection from Windows and Mac systems. If you follow the steps correctly, you will be able to uninstall the unwanted application from Control Panel, erase the unnecessary browser extension, and eliminate files and folders related to RedProtection completely.Uninstall RedProtection from Windows
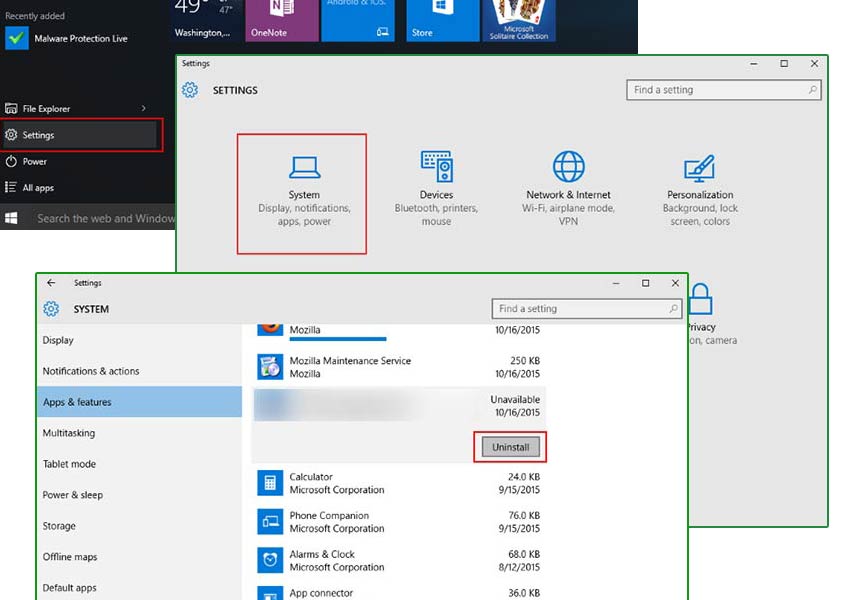
Windows 10
- Click on Start and select Settings
- Choose System and go to Apps and features tab
- Locate the unwanted app and click on it
- Click Uninstall and confirm your action
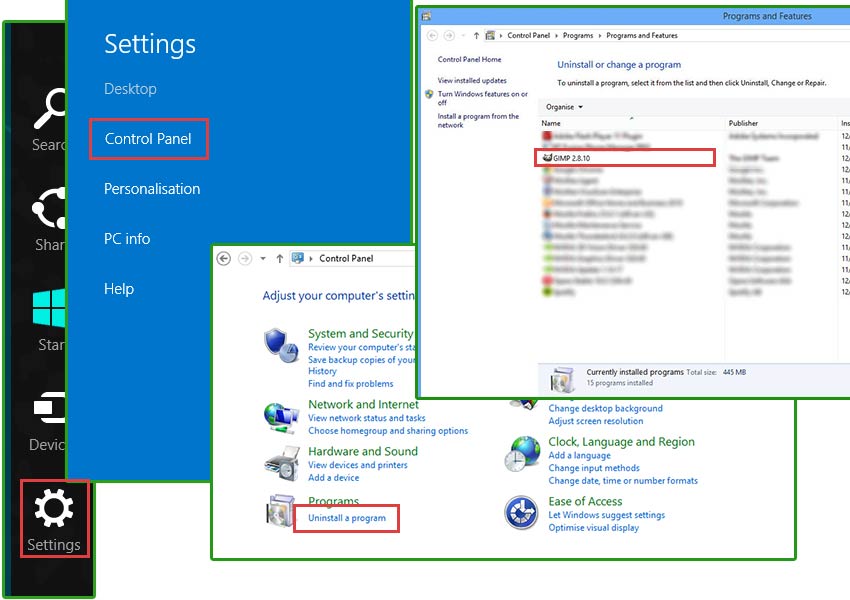
Windows 8/Windows 8.1
- Press Win+C to open Charm bar and select Settings
- Choose Control Panel and go to Uninstall a program
- Select the unwanted application and click Uninstall
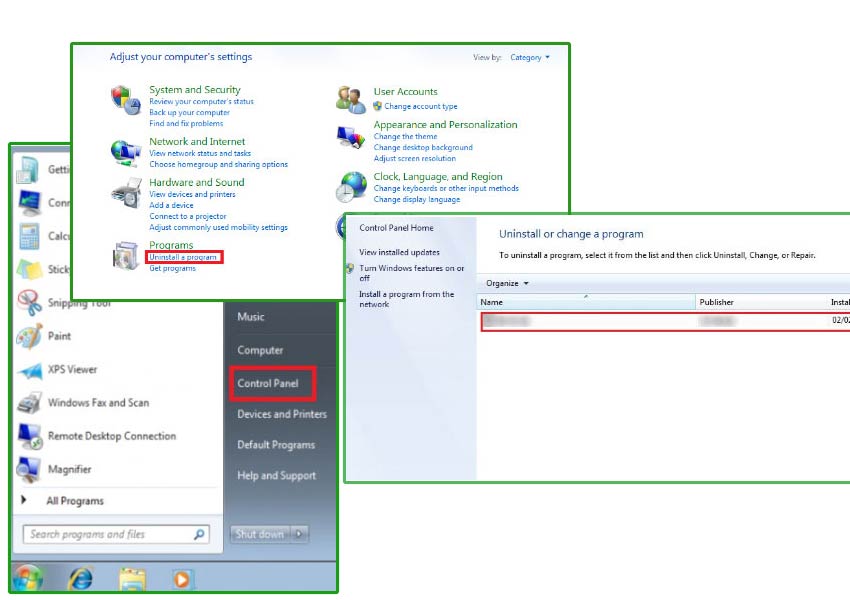
Windows 7/Windows Vista
- Click on Start and go to Control Panel
- Choose Uninstall a program
- Select the software and click Uninstall
Windows XP
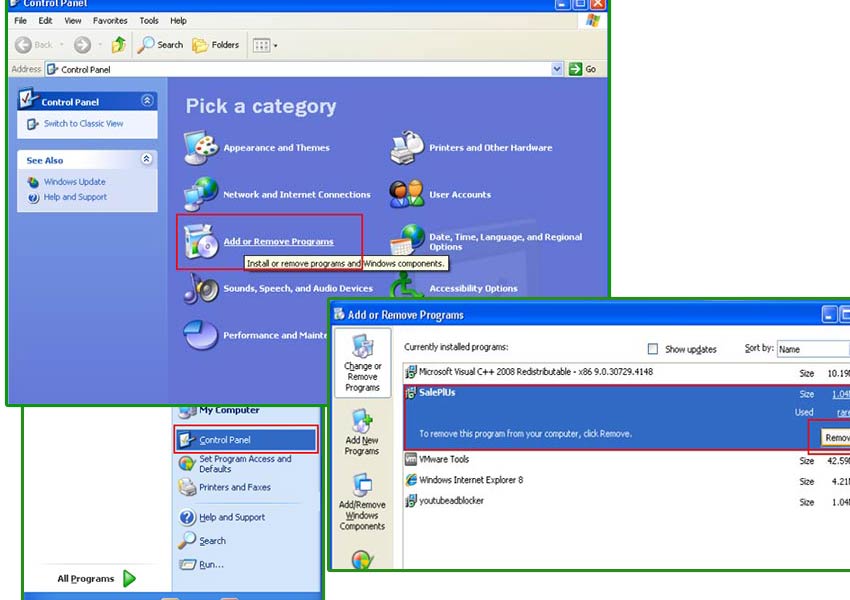
- Open Start menu and pick Control Panel
- Choose Add or remove programs
- Select the unwanted program and click Remove
Eliminate RedProtection extension from your browsers
RedProtection can add extensions or add-ons to your browsers. It can use them to flood your browsers with advertisements and reroute you to unfamiliar websites. In order to fully remove RedProtection, you have to uninstall these extensions from all of your web browsers.Google Chrome
- Open your browser and press Alt+F
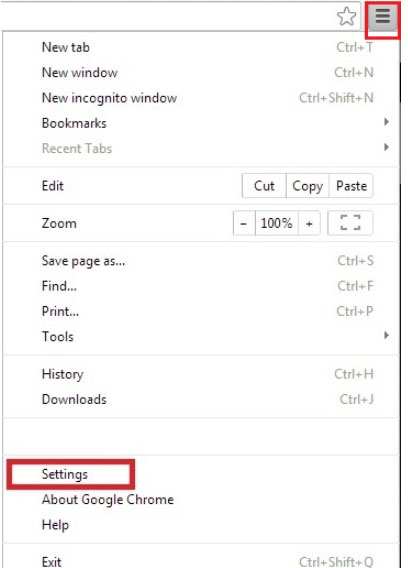
- Click on Settings and go to Extensions
- Locate the RedProtection related extension
- Click on the trash can icon next to it
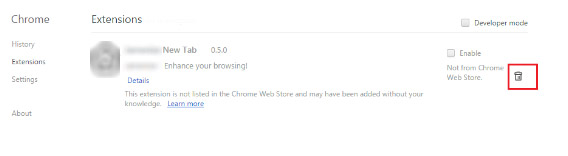
- Select Remove
Mozilla Firefox
- Launch Mozilla Firefox and click on the menu
- Select Add-ons and click on Extensions
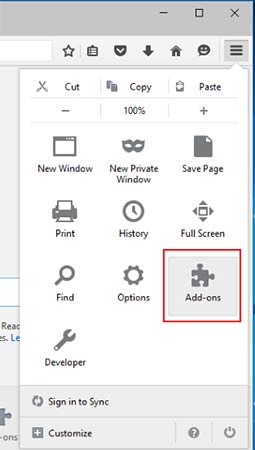
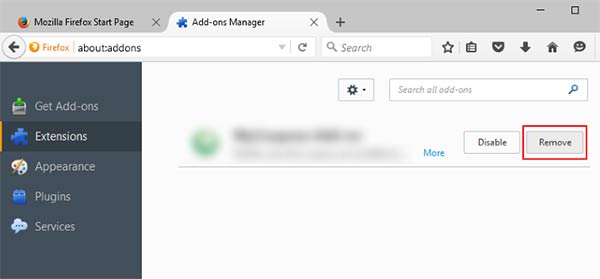
- Choose RedProtection related extension
- Click Disable or Remove
Internet Explorer
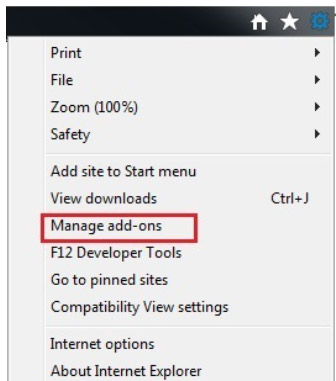
- Open Internet Explorer and press Alt+T
- Choose Manage Add-ons
- Go to Toolbars and Extensions
- Disable the unwanted extension
- Click on More information
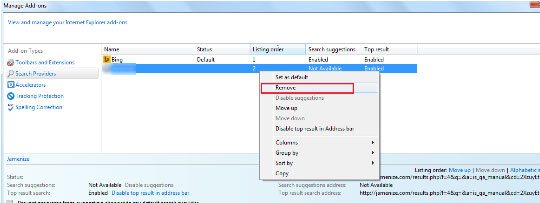
- Select Remove
Restore your browser settings
After terminating the unwanted application, it would be a good idea to reset your browsers.Google Chrome
- Open your browser and click on the menu
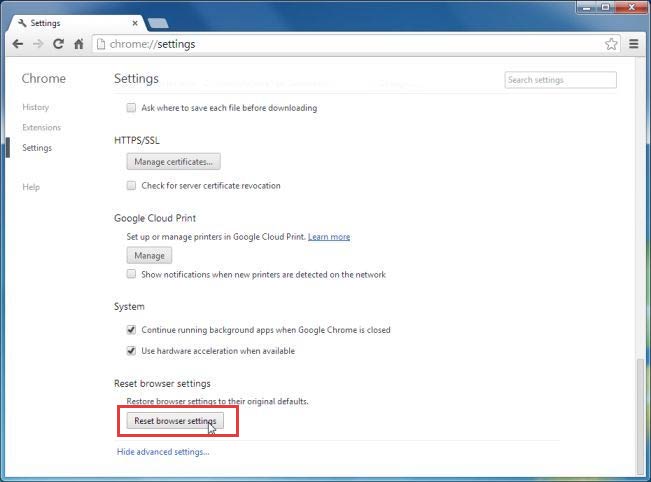
- Select Settings and click on Show advanced settings
- Press the Reset settings button and click Reset
Mozilla Firefox
- Open Mozilla and press Alt+H
- Choose Troubleshooting Information
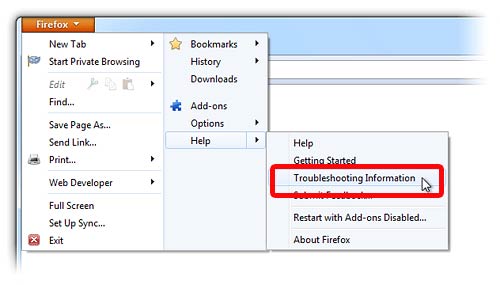
- Click Reset Firefox and confirm your action
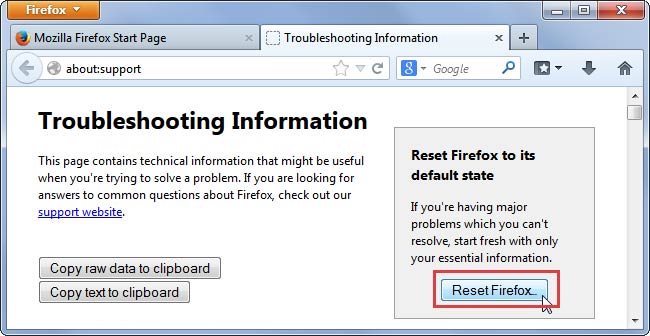
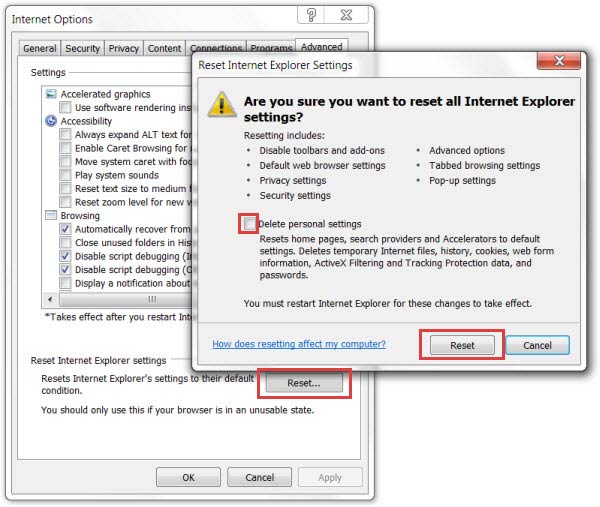
Internet Explorer
- Open IE and press Alt+T
- Click on Internet Options
- Go to the Advanced tab and click Reset
- Enable Delete personal settings and click Reset