Eliminate the files usinG the manual method
Joker (also known as JokerRansomware) not only encrypts images, media files, archives, documents, and other sensitive files but also corrupts the files of downloaded applications. For instance, the Joker is able to log keystrokes and write all in one record. Unfortunately, those Joker notifications have little to do with this tech giant. You may wonder why it has been tagged as ransomware if it doesn’t lock files. However, be cautioned that declarations display that criminals hardly keep their word. User must examine his pc together with credible and useful malware removal program if he has any declarations relating to this malware. Instead of spread your income in bundles with crooks.

JokerVideoJoker is a contamination to person’s privacy and safety. At least, in other words the encryption algorithm noted in the ransom message that the fineware exhibits. All these issues are distribute by accidentally as you could have believed, this attachment possesses either the document that starts the download of the ransomware when launching or earlier harbors the primary executable. For instance, it could be called “holy.jpg.exe.” as this spam mail may state to come from a well-know establishment, a government office, or your bank, you would not have concerns connected to its credibility initially notice, which can, nuturally, recover you the afterwards headache of removing Joker and presumably giving up your valuable files. You moreover won’t be capable to entry certain sites too as Joker Trojan merely safeguards itself from being eliminated from the pc.
Download Removal Toolto remove JokerFix the MBR (Master Boot catalog)
If Joker Ransomware were to run, then it would encode your files together with an advanced cipher that the cyber criminals call ./Joker cipher. After that, it is started in an automatic way, and it begins encoding your files quickly. However, all this procedure may take only a couple moments tops. They might easily acquire up false senders and subject lines that may trick you. That is possibly since the ransomware encodes a load of .Exe files, and the device can not load them anymore. Of course, those attachments sound wholly not malicious, for instance, they may mirror documents or invoices.
The absolute removal of Joker must be performed as shortly because this malicious virus is discovered on your private os. Employ the guidelines that we provide beneath, but follow them closely as a single missed stage might bring about stays of Joker. Unfortunately, the ransom notice in the .Txt catalog is fewer descriptive than the user interface of the parasite. Should you choose to Joker in a manual way, you shall should eliminate a dangerous file in a folder i.e. best to acquire rid of as well. In other cases, leftovers may be regardless accustomed for its damaging functionality. Shutting down in 60 minutes.
Joker the ransomware malware
In this notification you are warned about the unlucky breach and that “the malicious application has enchiphered all of the files that are present on this operating system.” the cyber criminals plus recommend you a chance to buy their one-of-a-kind decryption tool for $300. IT researcher Matthieu Suiche detected that the Joker3.0 ransomware connects to ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com, which was as promptly as you can bought and registered to avoid the distribution. However, we can’t be one hundred percentage certain that the same indications would run on up-to-date or new Joker variations. It would aid you in detecting the infection’s malign info on the computer and remove it in an automatic way. .Id-< The free-of-charge variation of this utility may be collected from our page by pressing on the Download button. The ".Tar" add-on is a regular archive log for Linux OS, but, evidently, these kinds of are not concrete or legitimate archives.
Download Removal Toolto remove JokerAs noted, elimination in a manual way is nearly not possible for the ordinary user, and even advanced user entire struggle in packages with it. The configuration targets of this threat are the following: But there is regardless some predicament to clear up. So we suggest that you Joker. .Txt, imgdesktop.exe, a record along with an odd name (e.g., sdajfhdfkj). This can’t be reported to be a steep fee for your valuable files if you genuinely get the fundamental key and files to save them. Therefore, we advise that you Joker promptly.
Manual Joker removal
Below you will find instructions on how to delete Joker from Windows and Mac systems. If you follow the steps correctly, you will be able to uninstall the unwanted application from Control Panel, erase the unnecessary browser extension, and eliminate files and folders related to Joker completely.Uninstall Joker from Windows
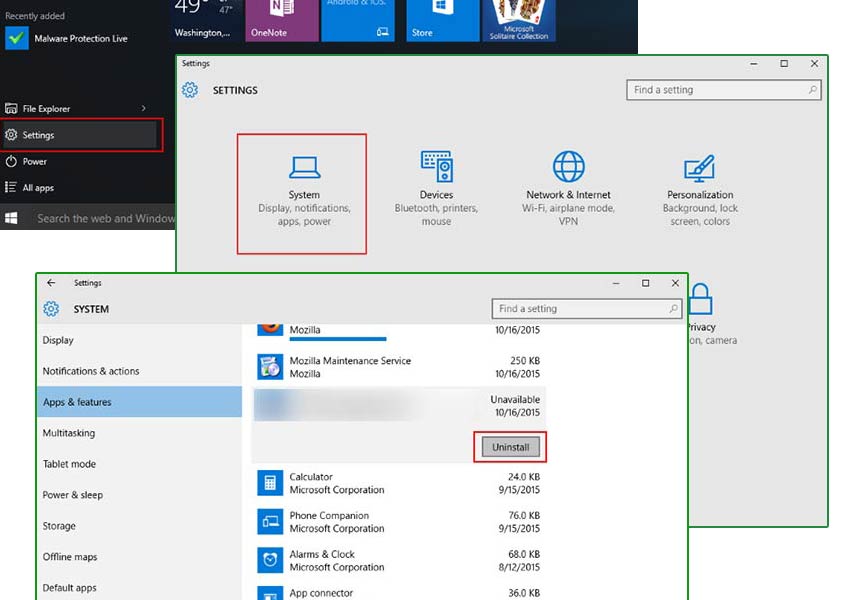
Windows 10
- Click on Start and select Settings
- Choose System and go to Apps and features tab
- Locate the unwanted app and click on it
- Click Uninstall and confirm your action
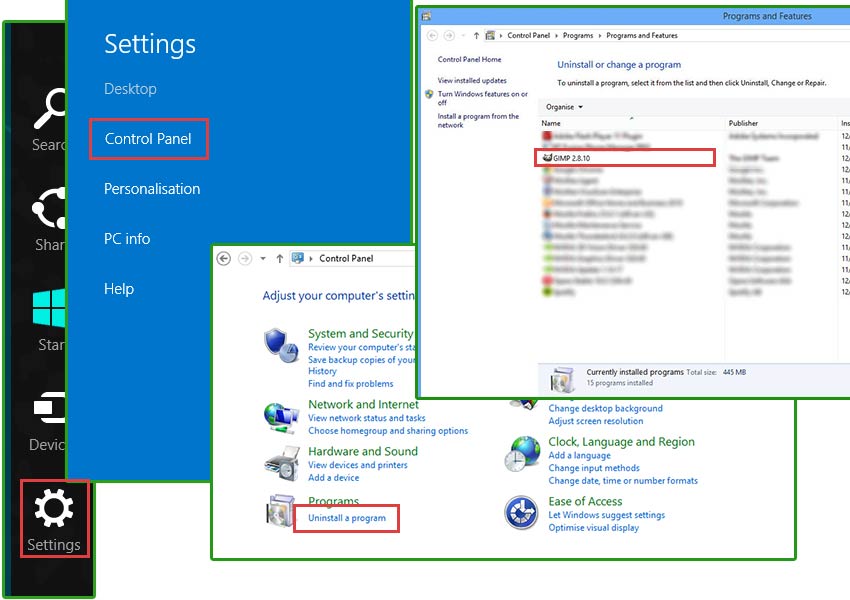
Windows 8/Windows 8.1
- Press Win+C to open Charm bar and select Settings
- Choose Control Panel and go to Uninstall a program
- Select the unwanted application and click Uninstall
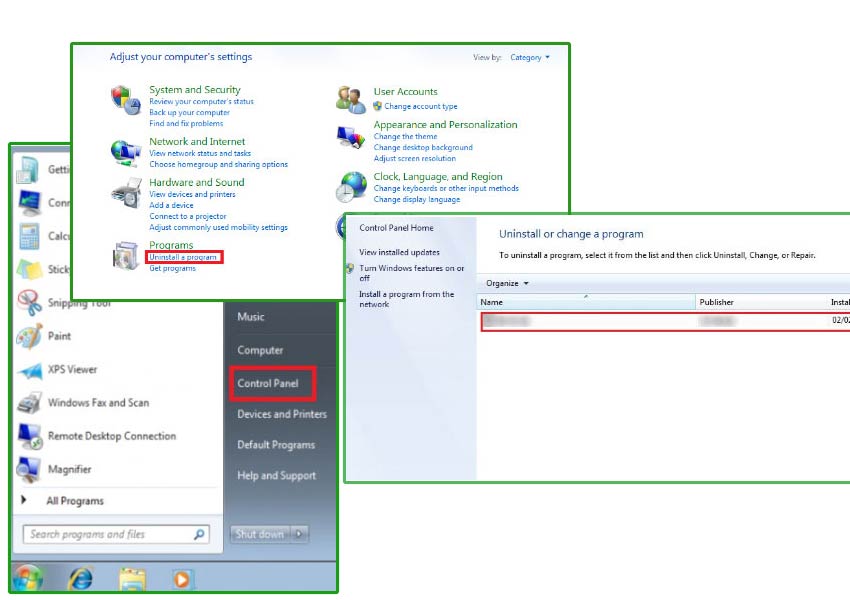
Windows 7/Windows Vista
- Click on Start and go to Control Panel
- Choose Uninstall a program
- Select the software and click Uninstall
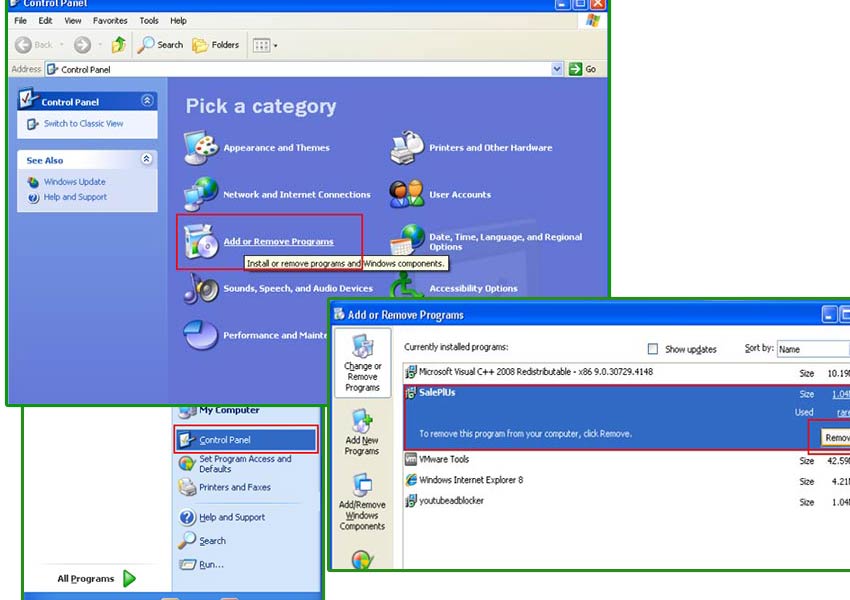
Windows XP
- Open Start menu and pick Control Panel
- Choose Add or remove programs
- Select the unwanted program and click Remove
Eliminate Joker extension from your browsers
Joker can add extensions or add-ons to your browsers. It can use them to flood your browsers with advertisements and reroute you to unfamiliar websites. In order to fully remove Joker, you have to uninstall these extensions from all of your web browsers.Google Chrome
- Open your browser and press Alt+F
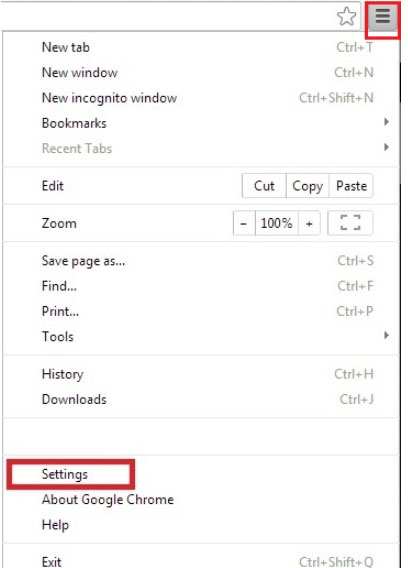
- Click on Settings and go to Extensions
- Locate the Joker related extension
- Click on the trash can icon next to it
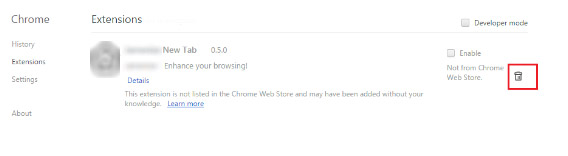
- Select Remove
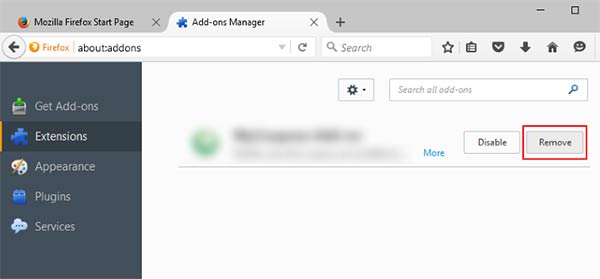
Mozilla Firefox
- Launch Mozilla Firefox and click on the menu
- Select Add-ons and click on Extensions
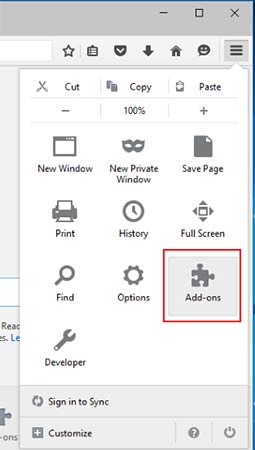
- Choose Joker related extension
- Click Disable or Remove
Internet Explorer
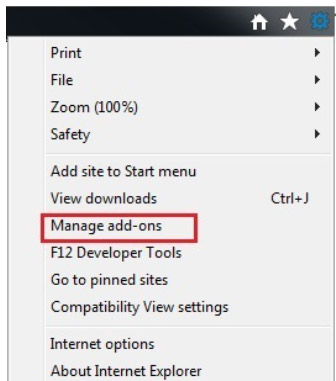
- Open Internet Explorer and press Alt+T
- Choose Manage Add-ons
- Go to Toolbars and Extensions
- Disable the unwanted extension
- Click on More information
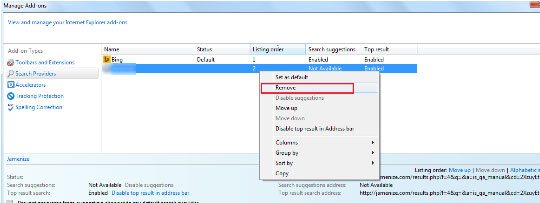
- Select Remove
Restore your browser settings
After terminating the unwanted application, it would be a good idea to reset your browsers.Google Chrome
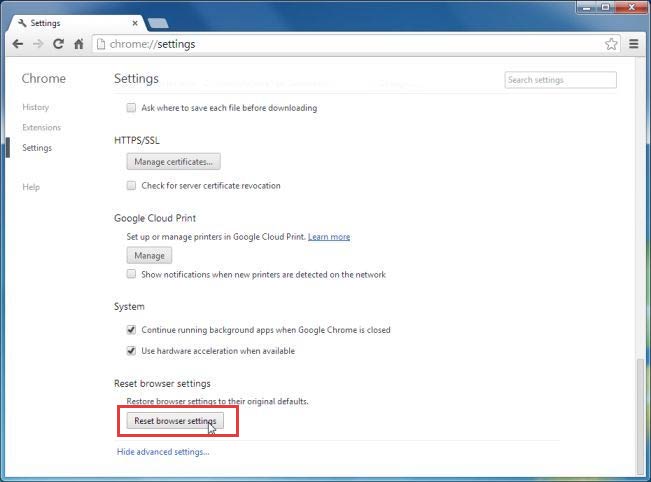
- Open your browser and click on the menu
- Select Settings and click on Show advanced settings
- Press the Reset settings button and click Reset
Mozilla Firefox
- Open Mozilla and press Alt+H
- Choose Troubleshooting Information
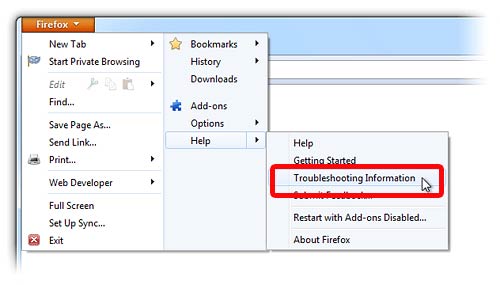
- Click Reset Firefox and confirm your action
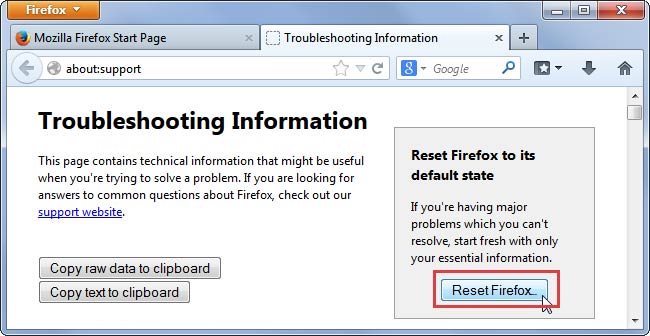
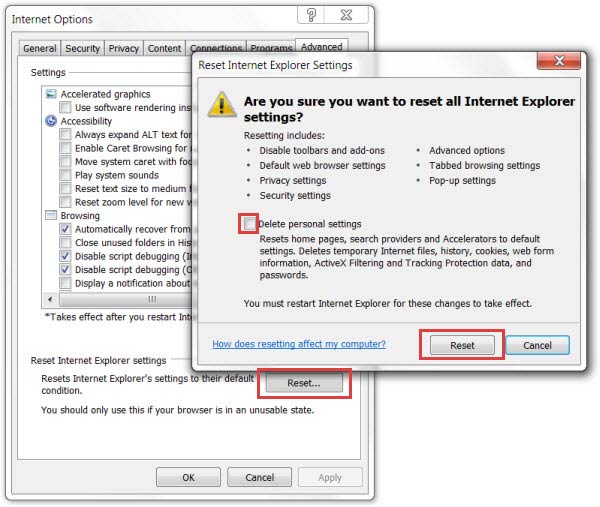
Internet Explorer
- Open IE and press Alt+T
- Click on Internet Options
- Go to the Advanced tab and click Reset
- Enable Delete personal settings and click Reset