Things you ought to know related to LEAKDB ransomware
LEAKDB travels by Trojan horse, which may easily intrude unsuccessfully safe machines. EAntivirus Pro isn’t even a powerful piece; Below no circumstances you ought to press the ‘Download’ button and permission to supply your private and money-related details! Plus called as Rocra, LEAKDB is an advanced software, that may relate not merely to workstations. Otherwise, it will maintain preventing your whole device and shall lurk lawful applications from you. You shall merely see that notification in the center of your machine screen alert you for quite some forbidden motions. Investigate consequences defense focus assist secure your machine Files detected 2353445 mistakes detected 234 Total mistakes 1267″ if you spot this note, do not believe it: Instead of paying 500 of Swedish Krona everywhere $75) as a penalty, you need to remove LEAKDB from your pc.

LEAKDB malware is one of the ransomwares that are distributed thru false modifies. The text, audio and video files, images and other document classifications are encoded together with the asymmetric cipher. What is etc., the malevolent application plus produced a backup of the catalog implanting another, How_To_Decrypt.txt add-on to it. Further details related to the payment operating system and other info are added merely after the victim contacts to cyber criminals. The latter key is the golden calf for the hackers. This catalog is noted to use a title of ‘funnypicture.jpg.exe’, but there can be other headings accustomed for aiming to fool etc. not aware PC people.
Download Removal Toolto remove LEAKDBHow to delete LEAKDB! Ransomware?
LEAKDB is responsible for numerous damaging activities on operating systems of infected computers. LEAKDB makes use of the headings of legal police establishments so to earn people faith it. So to stop this matter, files, you ought to attempt backup or such catalog retrieval instruments as R-Studio in addition, the daunting LEAKDB itself shall be forwarded to your desktop background and press you to contact the email address of cyber crooks. To block this from taking place, we firmly advise you to avoid doubtful web pages. Unfortunately, there is no way to restore the locked files without paying. An unfortunate person is notified via a penalty letter and a application, intended for decryption of files. What is etc., LEAKDB can entry and enchipher information stored on external drives that are plugged onto your device.
Speaking of ransomware, crooks normally ask the victim to utilize a Tor group and to pay the fine via untraceable Bitcoin payment device. You may try that way as well. For this logic, you ought to never download free software from dubious computer network websites, and if you do so – set up it alongside alert. Social networking pages, forums, email accounts can be bombarded with spam letters that have web links or attachments. Anti-malicious software program, in this situation, it is smart to set up an anti-malware tool, for instance, Anti-malicious software program, which will locate the viruses. In addition, stop pop-up ads suggesting you to get updates for Java, Flash Player and akin programs.
How is LEAKDB! Ransomware scattered?
We cannot say that there is a guaranteed method to restore all of the files, encrypted by LEAKDB ransomware. LEAKDB It has been a common way for the up-to-date contaminations as well. If you are going thru this endure right away, you ought to restart your LEAKDB pc onto sheltered settings former running BullGuard Mobile safety: it can discover and erase all evil LEAKDB ransomware files. So, henceforth, begin via USB external troublesome drives, CDs, DVDs, Google Drive, Dropbox, Flickr or any other remedy.
Download Removal Toolto remove LEAKDBIt’s always less difficult to stop LEAKDB ransomware breach somewhat that manage its results after it ravages your computer system. These kinds of might be able to eliminate all variants of LEAKDBó LEAKDB malicious software, but shall not run if your not easy drive is enchiphered. If one of the accounts has administrator rights, you ought to be capable to begin anti-malicious software software. However, you need to realize that it doesn’t decode the enchiphered files, so you shall need to repair them either from an existing back-up or faith for details retrieval tools to figure out. Contaminated in addition to Trojans, that can download etc. viruses on your os.
Manual LEAKDB removal
Below you will find instructions on how to delete LEAKDB from Windows and Mac systems. If you follow the steps correctly, you will be able to uninstall the unwanted application from Control Panel, erase the unnecessary browser extension, and eliminate files and folders related to LEAKDB completely.Uninstall LEAKDB from Windows
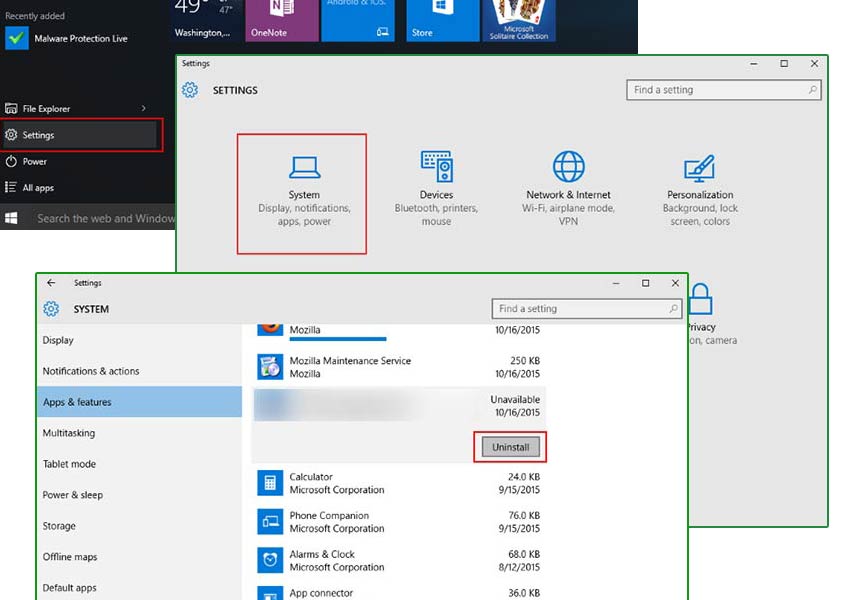
Windows 10
- Click on Start and select Settings
- Choose System and go to Apps and features tab
- Locate the unwanted app and click on it
- Click Uninstall and confirm your action
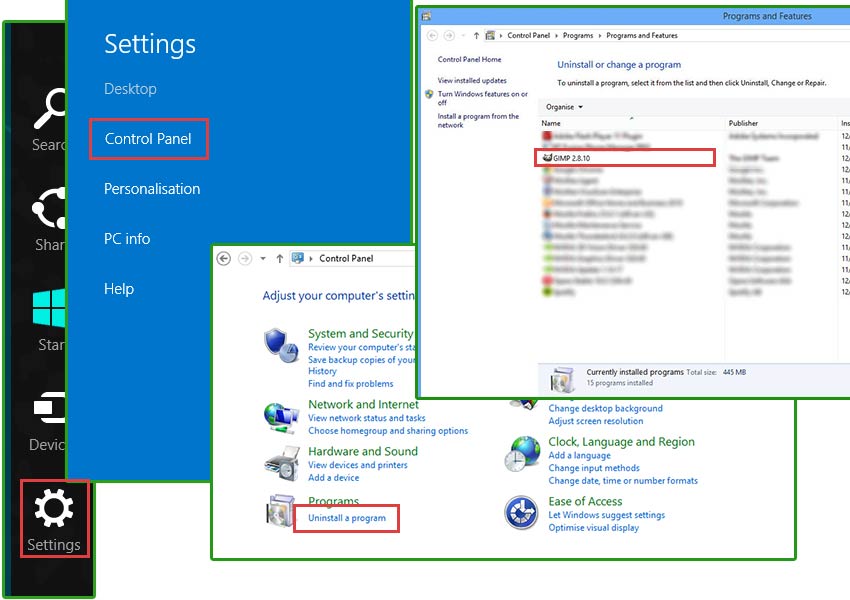
Windows 8/Windows 8.1
- Press Win+C to open Charm bar and select Settings
- Choose Control Panel and go to Uninstall a program
- Select the unwanted application and click Uninstall
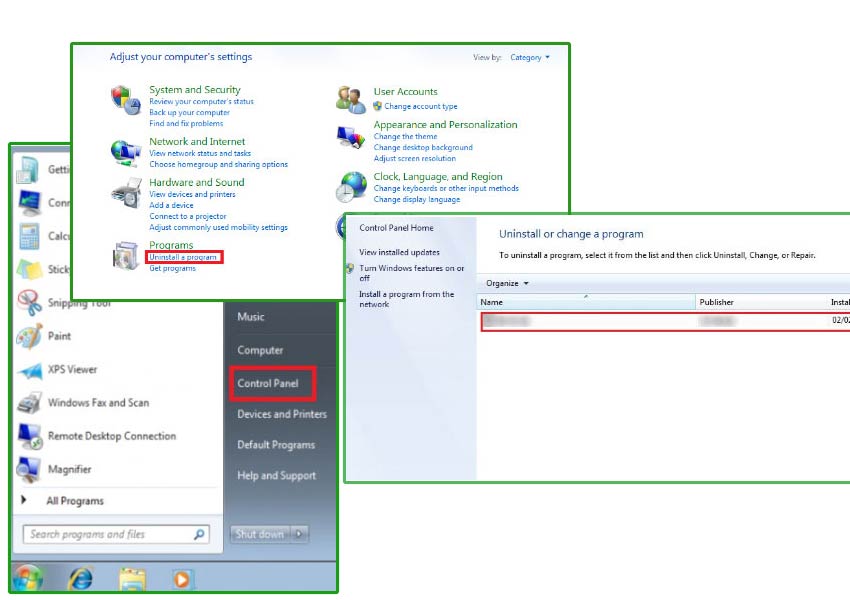
Windows 7/Windows Vista
- Click on Start and go to Control Panel
- Choose Uninstall a program
- Select the software and click Uninstall
Windows XP
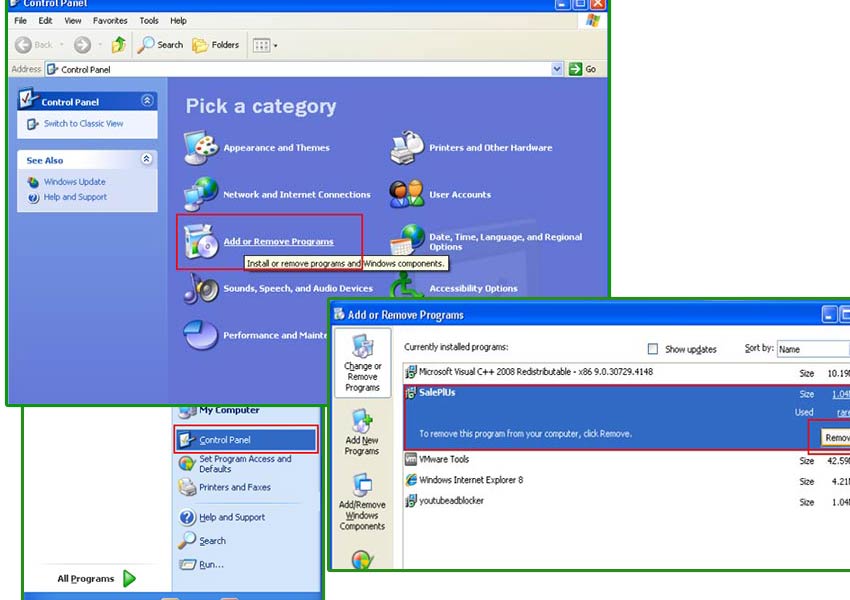
- Open Start menu and pick Control Panel
- Choose Add or remove programs
- Select the unwanted program and click Remove
Eliminate LEAKDB extension from your browsers
LEAKDB can add extensions or add-ons to your browsers. It can use them to flood your browsers with advertisements and reroute you to unfamiliar websites. In order to fully remove LEAKDB, you have to uninstall these extensions from all of your web browsers.Google Chrome
- Open your browser and press Alt+F
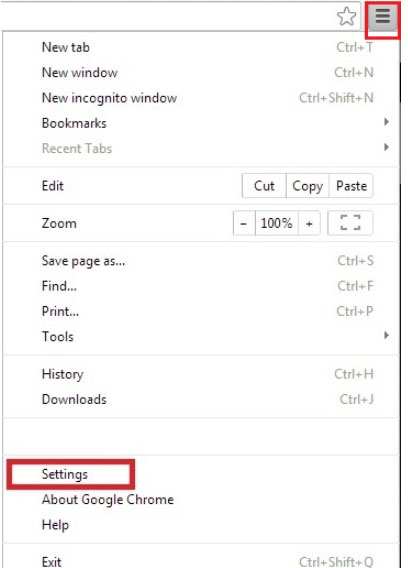
- Click on Settings and go to Extensions
- Locate the LEAKDB related extension
- Click on the trash can icon next to it
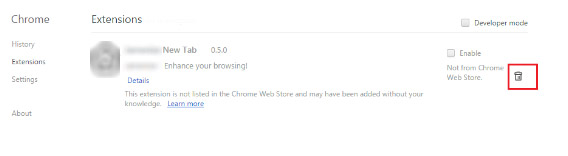
- Select Remove
Mozilla Firefox
- Launch Mozilla Firefox and click on the menu
- Select Add-ons and click on Extensions
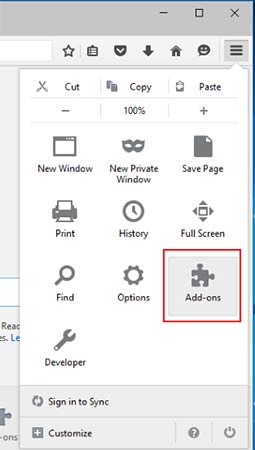
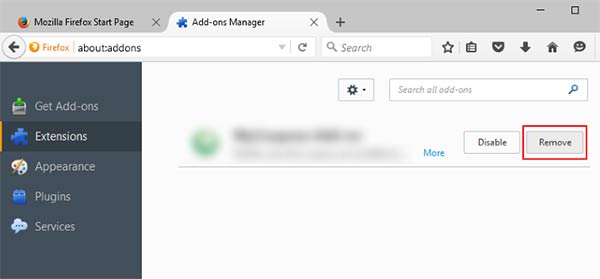
- Choose LEAKDB related extension
- Click Disable or Remove
Internet Explorer
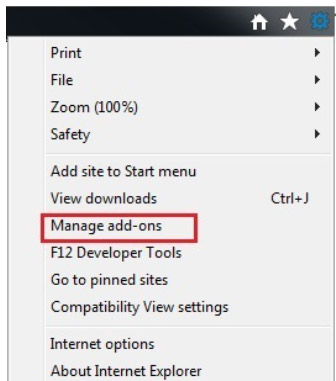
- Open Internet Explorer and press Alt+T
- Choose Manage Add-ons
- Go to Toolbars and Extensions
- Disable the unwanted extension
- Click on More information
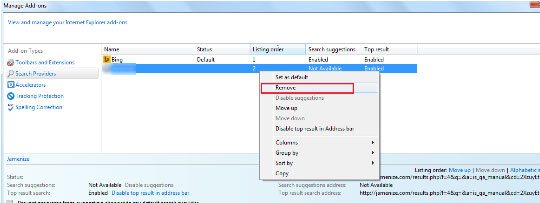
- Select Remove
Restore your browser settings
After terminating the unwanted application, it would be a good idea to reset your browsers.Google Chrome
- Open your browser and click on the menu
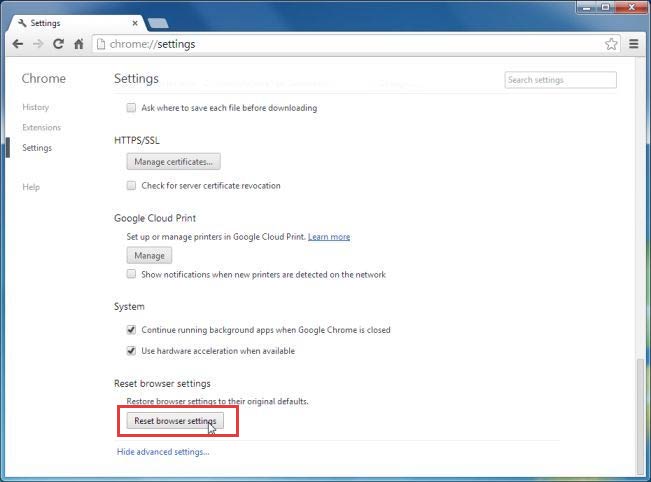
- Select Settings and click on Show advanced settings
- Press the Reset settings button and click Reset
Mozilla Firefox
- Open Mozilla and press Alt+H
- Choose Troubleshooting Information
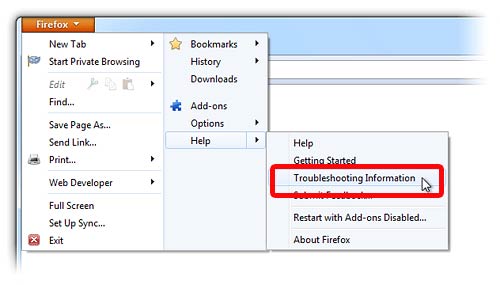
- Click Reset Firefox and confirm your action
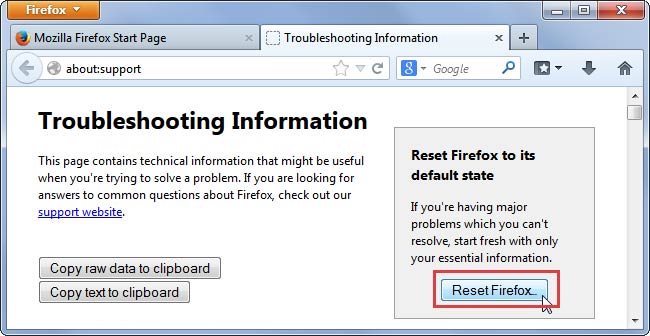
Internet Explorer
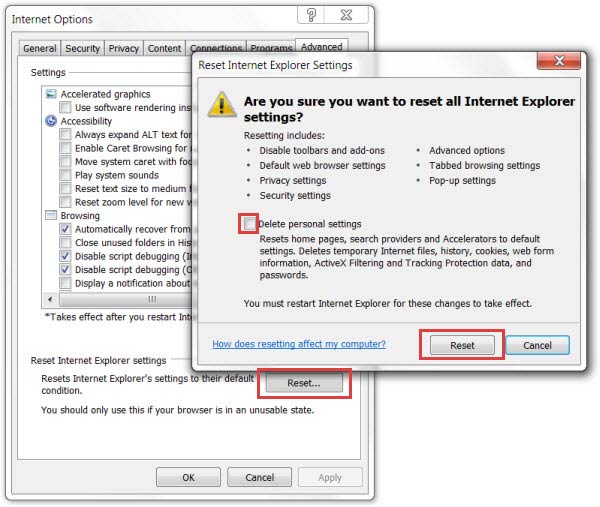
- Open IE and press Alt+T
- Click on Internet Options
- Go to the Advanced tab and click Reset
- Enable Delete personal settings and click Reset