Relating to Ppvs- Ppvs Ransomware
Ppvs virus is one more dangerous ransomware that locks personal files of computer users and asks them to pay a ransom if they want to retrieve their files. When working, Ppvs employs varying frighten ploys, e.g popups, pc alerts and simulated pc scans to threaten the user into purchasing the bogus complete variation of the software. Don’t download or buy this application and stop Ppvs’s domain via your HOSTS record. Rather than your frequent desktop screen, you will detect merely false notification stating that Police or other official authoity requires from you some profit. However, you must remember that Ppvs ESPAÑOLA malware is accustomed merely for robbing PC people, forcing them to pay a specific penalty so to decode their pcs. It could impair your personal computer and intrude on your privacy!

Ppvs is set up to oss by a Trojan malicious software. Haven’t ran into such frauds earlier, you might obtain effortlessly coerced by such notifications. If ransomware malicious software that we earlier were popular were generally targeting Windows platform and did not even keep an eye to the side of Linux or Mac OS, for now, people of these kinds of two platforms may also be involved. They are associated to you visiting unlawful sites, through and/or spreading child pornography and copyrighted content like music, shows. In point, this note appears hugely complicated and incorporates Ppvs’s symbols, victim’s IP address and other information. This alert states: If the infected device is running on a virtual drive and not a legitimate Windows environment, the malicious software will in an automatic way remove itself. We can without doubt locate this reference comprehensible as the ransomware malicious software is tried to be introduced as a fully complex malicious software.
Download Removal Toolto remove PpvsHow is Ppvs Ransomware distributed?
Mainly, there exists two solutions — automatic and by hand removal. Infections is generally additional to spam emails, so generally, you ought to not open any fishy email attachments, particularly those that come from unknown web pages. It’s just a malicious method used for earning illegal the encrypted file, the file size before its encryption, RSA-2048 encrypted encryption key, the size of the key and the identifier of Ppvs infection – the prefix. In addition, you should concentrate on spelling and typo errors. We advise installing Anti-threat application anti-threat program.
* people invaded in bundles with Ukash infections are authorized to entry other accounts on their Windows computers. Therefore, it is really important to shield your machine from infection by installing a wonderful computer security tool. They consist of a .Zip document which adds unclean file, for instance, PAYMENT.vbs, PAYCHECK.vbs, PENALTY.vbs. However, should you choose getting applications from unknown web pages or not trustworthy catalog-distribution sites, you might easily end up with an alarming machine threat. Although you force a web surfr to close down via responsibility owner, the next time you surf ‘Ppvs’ message will appear again. If none of these kinds of approaches operated for you, do the following:
In the Case of Ppvs Ransomware parasite
If you don’t use pc fix choice on your computer system, there is a possibility to enforce shadow replicate snapshots. For that you can make use of previous noted software. Thus, certain security programs may bypass the infection which will mask the ransomware inside. But don’t you dare kneel down former those crooks, specially, whenever you can nearly smell the decryptor to be created. After doing that, carry out an entire os scan with anti-infection utility. Read the last section to tell the likely approaches to carry out that.
Download Removal Toolto remove PpvsThere are 2 variations of the ransomwares through .Ppvs add-on : Try to refuse the Flash to generate your ransomware prevent run as designed. Or in addition, you have to have the most recent version of the anti-malicious software software for it to erase Ppvs successfully. After doing that, execute an entire computer scan with anti-infections tool. When it comes to decryption of enchiphered statistics, you could identify a proper record decryption program. You are dealing with an alarming system malware, so you ought to manage it in a capable way.
Manual Ppvs removal
Below you will find instructions on how to delete Ppvs from Windows and Mac systems. If you follow the steps correctly, you will be able to uninstall the unwanted application from Control Panel, erase the unnecessary browser extension, and eliminate files and folders related to Ppvs completely.Uninstall Ppvs from Windows
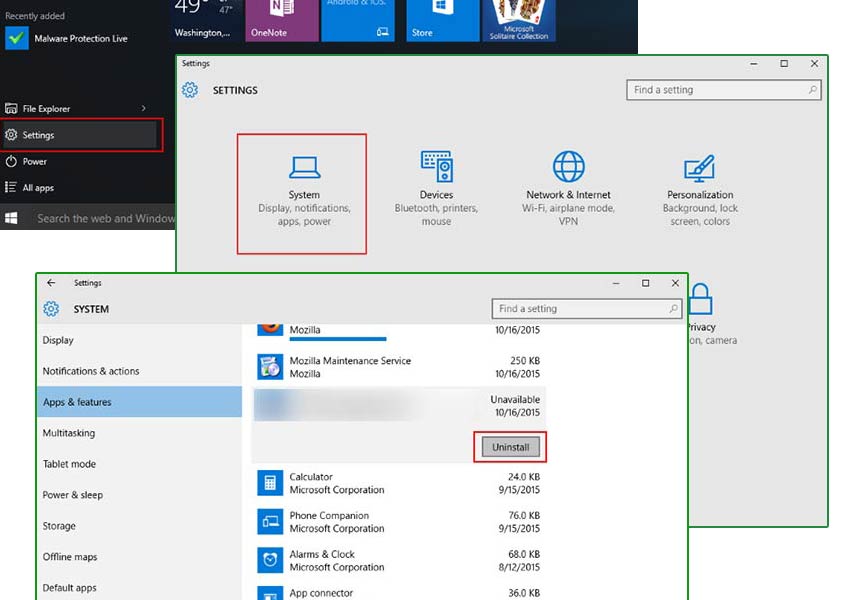
Windows 10
- Click on Start and select Settings
- Choose System and go to Apps and features tab
- Locate the unwanted app and click on it
- Click Uninstall and confirm your action
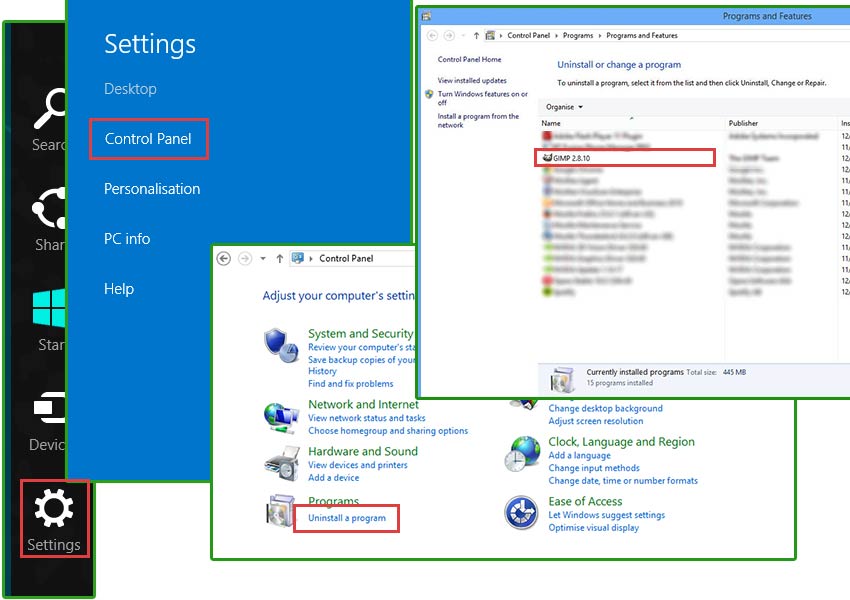
Windows 8/Windows 8.1
- Press Win+C to open Charm bar and select Settings
- Choose Control Panel and go to Uninstall a program
- Select the unwanted application and click Uninstall
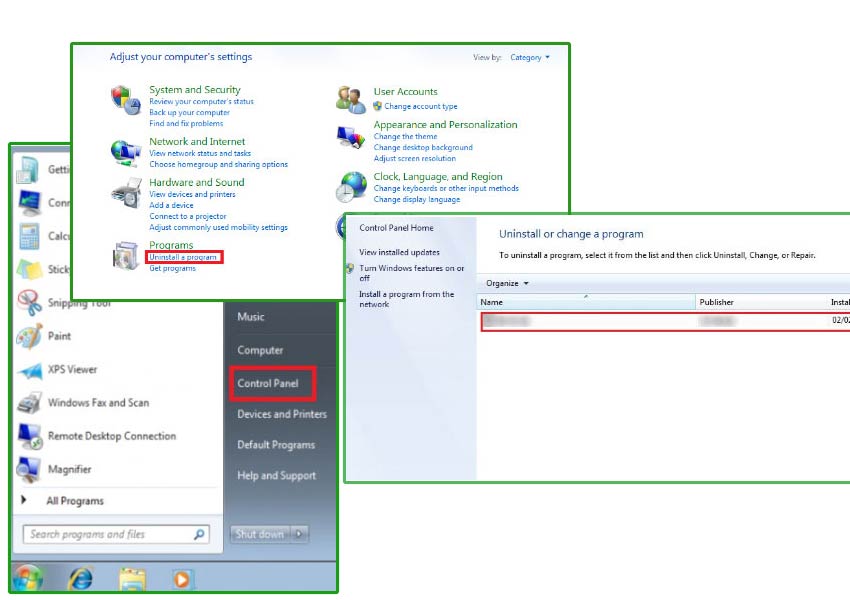
Windows 7/Windows Vista
- Click on Start and go to Control Panel
- Choose Uninstall a program
- Select the software and click Uninstall
Windows XP
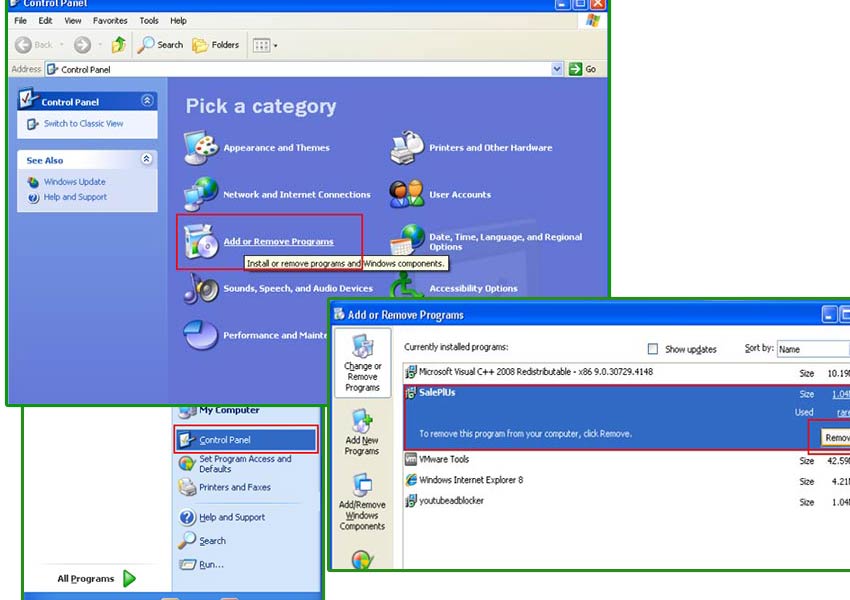
- Open Start menu and pick Control Panel
- Choose Add or remove programs
- Select the unwanted program and click Remove
Eliminate Ppvs extension from your browsers
Ppvs can add extensions or add-ons to your browsers. It can use them to flood your browsers with advertisements and reroute you to unfamiliar websites. In order to fully remove Ppvs, you have to uninstall these extensions from all of your web browsers.Google Chrome
- Open your browser and press Alt+F
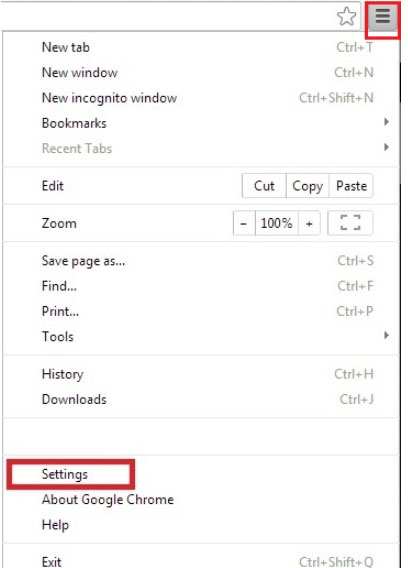
- Click on Settings and go to Extensions
- Locate the Ppvs related extension
- Click on the trash can icon next to it
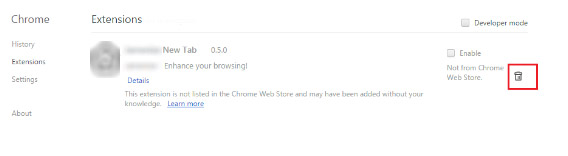
- Select Remove
Mozilla Firefox
- Launch Mozilla Firefox and click on the menu
- Select Add-ons and click on Extensions
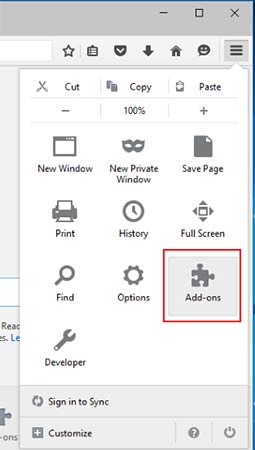
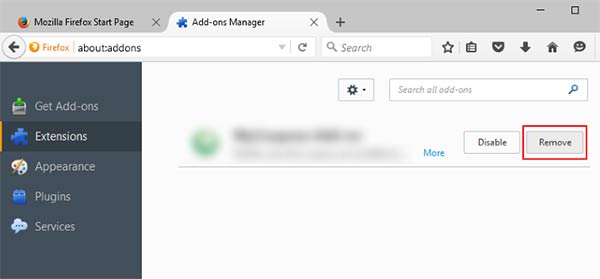
- Choose Ppvs related extension
- Click Disable or Remove
Internet Explorer
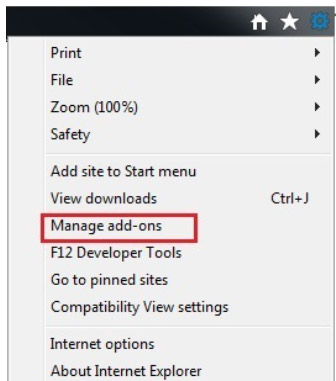
- Open Internet Explorer and press Alt+T
- Choose Manage Add-ons
- Go to Toolbars and Extensions
- Disable the unwanted extension
- Click on More information
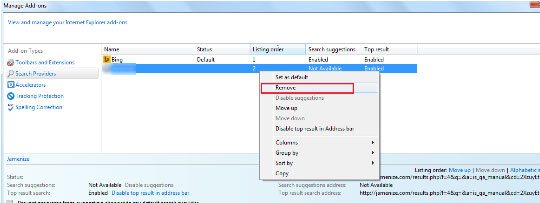
- Select Remove
Restore your browser settings
After terminating the unwanted application, it would be a good idea to reset your browsers.Google Chrome
- Open your browser and click on the menu
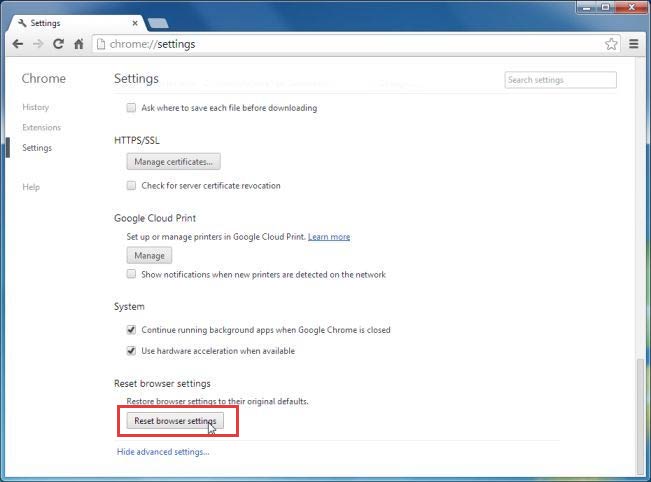
- Select Settings and click on Show advanced settings
- Press the Reset settings button and click Reset
Mozilla Firefox
- Open Mozilla and press Alt+H
- Choose Troubleshooting Information
- Click Reset Firefox and confirm your action
Internet Explorer
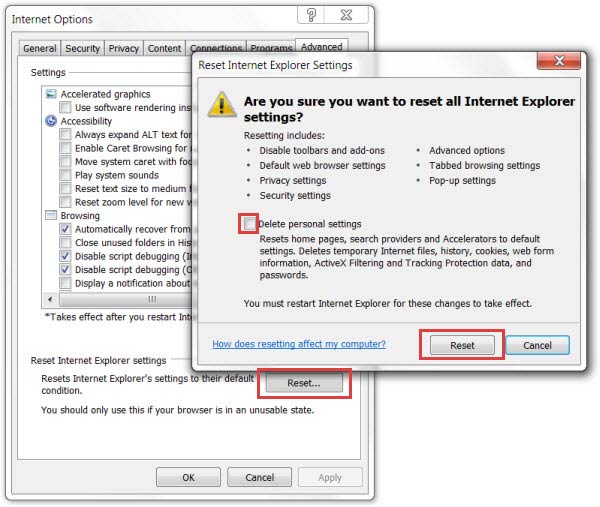
- Open IE and press Alt+T
- Click on Internet Options
- Go to the Advanced tab and click Reset
- Enable Delete personal settings and click Reset