About .Ldhy
Ldhy generally hijacks oss together with Trojan malware. Even etc., you ought to never take this software greatly and feel that it belongs for your local governmental establishment (police). It indicates that you are about to be deceived into believing that you are getting a sheltered log when actually you are about to download and set up a harmful Ldhy regardless, there are additional approaches how Ldhy could be circulated: The ransomware was detected the take much time week, i.e. below October – at the start of November, 2016. Supposedly, this key could be obtained solely from the infection publishers and implemented to restore enchiphered details. comodo@execs.com, help@ausi.com, heinz@oaht.com, numbaza@seznam.cz, sos@ausi.com, zanzibar@umpire.com, anna_stepanova@aol.com, byaki_buki@aol.com, evromaidan2014@aol.com, kolobocheg@aol.com, moshiax@aol.com, oduvansh@aol.com, etc.
 Download Removal Toolto remove Ldhy
Download Removal Toolto remove Ldhy
Ldhy has been actively circulating everywhere recently. This false pc optimization tool is spread using its official site, but it could in addition come into the device in packages without any knowledge invited in tandem with other software and files. In this case, security analysts highly suggest checking pc with good anti-spyware, such as If they call it, they can get bothered after receiving an redundant receipt from their actually, it is just an try to embezzles you. The text file which appears in the folders of encrypted files is called ReadMe.TxT. The contaminated log shall sound something like this: if the computer’s speed has left down seriously, you need to inspect it for Ldhy. There are applications like PhotoRec or R-studio for numbers retrieval aims.
How to restore the log encoded by Ldhy Ransomware?
If your browser was halted by ‘Ldhy’, guarantee to forget this false warning. The latter take advantage of kit manages on malicious pages and ad-supported windows which direct to these sites. We firmly advise removing it from touched PC computer promptly. Anti-viruses utility, if you oftentimes backup your statistics, store it on external storage drive and unplug the drive from your machine when you are not through it, you ought to be capable of keeping your files sheltered. This malware has little in common alongside the authentic police office. You ought to better say no to to offer it to them. Finally, keep a backup copy of your facts.
* people compromised in bundles with Ukash infections are authorized to entry other accounts on their Windows oss. Are permitted to entry other accounts on their Windows oss. Overview whether you are able to you restart your device to sheltered settings in bundles with networking or sheltered settings in bundles with command urge and monitor those stages: If none of those ways ran for you, do the following: But if you do not feel comfortable sufficient for the non-automatic malware elimination or merely do not want to waste your time, count on the malware removal tool programs to carry out the chore for you. also wishes that their victims would contact depositthere@e-mail.ph.
Download Removal Toolto remove LdhyHow to decipher Files enchiphered by Ldhy Ransomware?
RakhniDecryptor by KasperskyLab has turned out to be efficient in certain situations of ..Id-unintended number_”@” malicious software. Our recommendation is either via Bootable antivirus utility CD/USB disk and examining in bundles with it or calling +1-888-334-2444 (USA / CA ) for assistance. Are permitted to entry other accounts on their Windows operating systems. A ordinary anti-spyware tool is most often insufficient since there are countless malware distributing everywhere and striving to slither into onto operating systems all the time. In addition, R-Studio Either one of these apps should detect and remove In fact, removing Ldhy virus is important in any way.
Each time you the pc is started, the ransomware is activated and new files are being erased. If your inbox periodically gains letters that are absurd, then it may be that you are being oriented by author of ransomware. Menu, data must be copied, and So, you should be particularly careful about opening any attachments that come from unknown sources and are accompanied by suspicious emails. Make use of Anti-infections Tool, Anti-infections program or Anti-infections program automatic virus removal software to succeed in this task. I.e. why
Manual Ldhy removal
Below you will find instructions on how to delete Ldhy from Windows and Mac systems. If you follow the steps correctly, you will be able to uninstall the unwanted application from Control Panel, erase the unnecessary browser extension, and eliminate files and folders related to Ldhy completely.Uninstall Ldhy from Windows
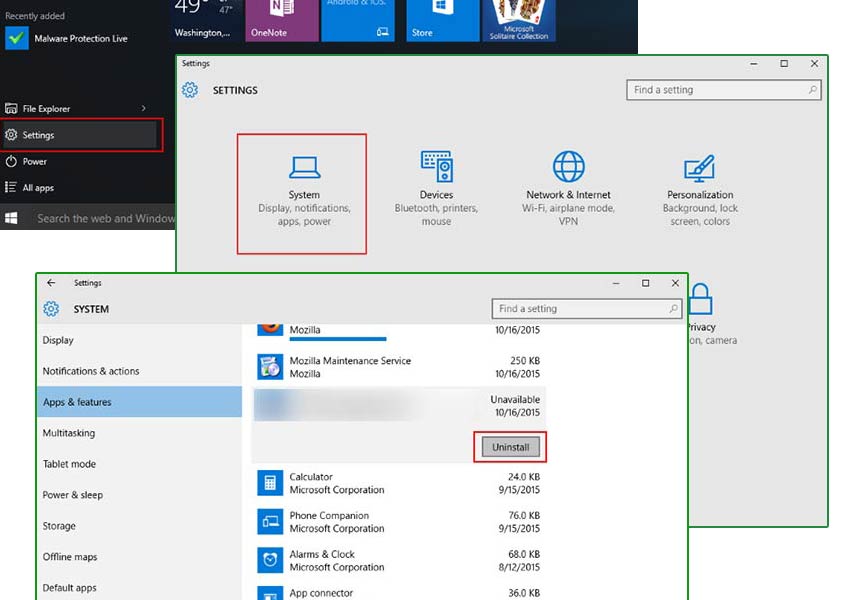
Windows 10
- Click on Start and select Settings
- Choose System and go to Apps and features tab
- Locate the unwanted app and click on it
- Click Uninstall and confirm your action
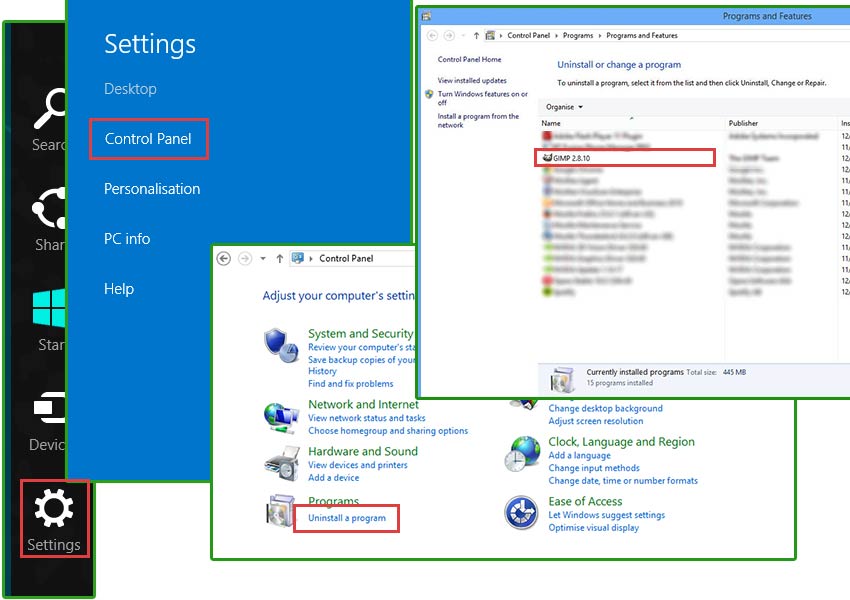
Windows 8/Windows 8.1
- Press Win+C to open Charm bar and select Settings
- Choose Control Panel and go to Uninstall a program
- Select the unwanted application and click Uninstall
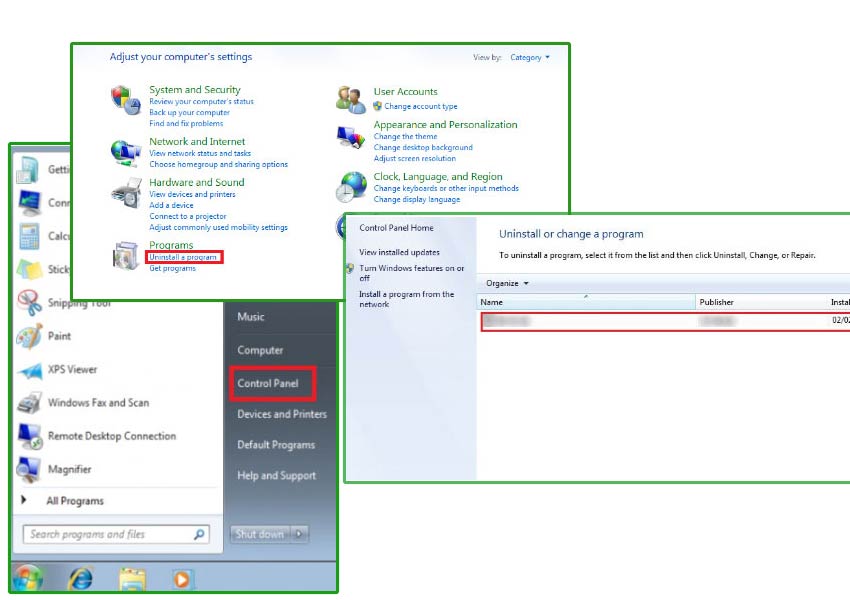
Windows 7/Windows Vista
- Click on Start and go to Control Panel
- Choose Uninstall a program
- Select the software and click Uninstall
Windows XP
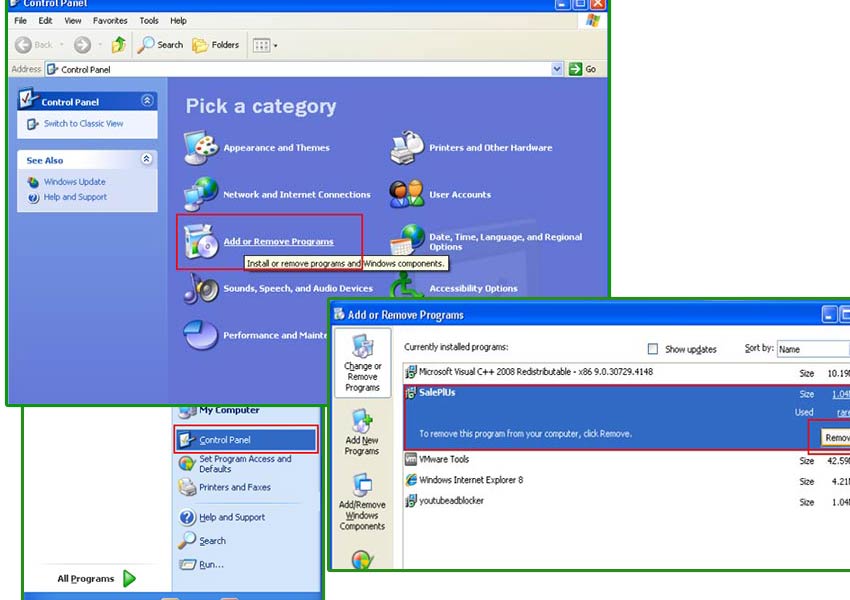
- Open Start menu and pick Control Panel
- Choose Add or remove programs
- Select the unwanted program and click Remove
Eliminate Ldhy extension from your browsers
Ldhy can add extensions or add-ons to your browsers. It can use them to flood your browsers with advertisements and reroute you to unfamiliar websites. In order to fully remove Ldhy, you have to uninstall these extensions from all of your web browsers.Google Chrome
- Open your browser and press Alt+F
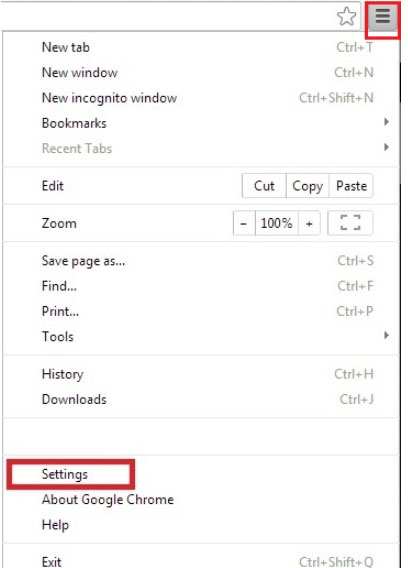
- Click on Settings and go to Extensions
- Locate the Ldhy related extension
- Click on the trash can icon next to it
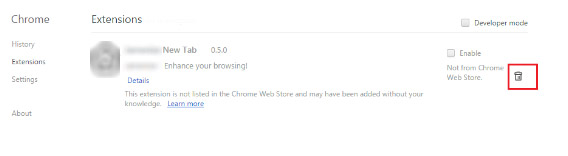
- Select Remove
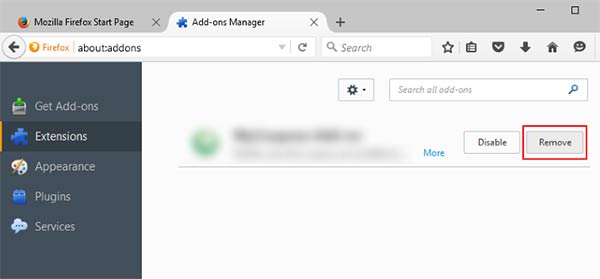
Mozilla Firefox
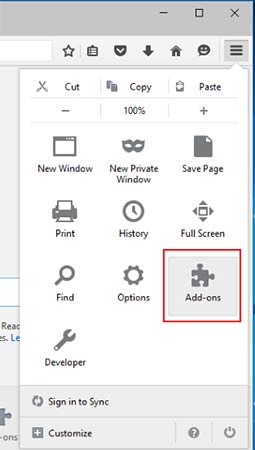
- Launch Mozilla Firefox and click on the menu
- Select Add-ons and click on Extensions
- Choose Ldhy related extension
- Click Disable or Remove
Internet Explorer
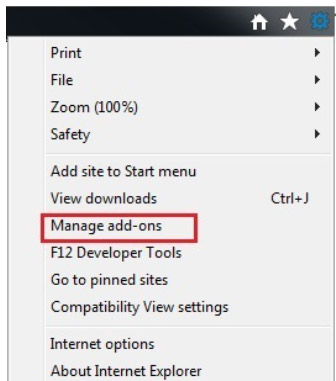
- Open Internet Explorer and press Alt+T
- Choose Manage Add-ons
- Go to Toolbars and Extensions
- Disable the unwanted extension
- Click on More information
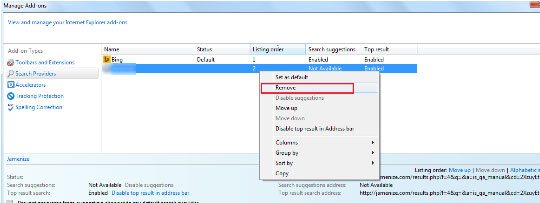
- Select Remove
Restore your browser settings
After terminating the unwanted application, it would be a good idea to reset your browsers.Google Chrome
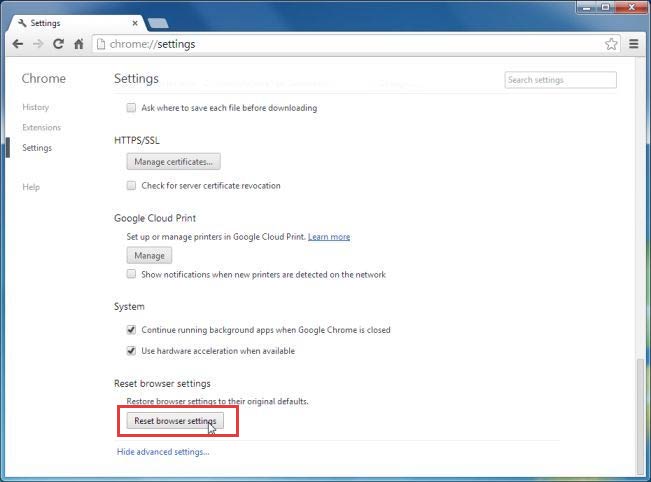
- Open your browser and click on the menu
- Select Settings and click on Show advanced settings
- Press the Reset settings button and click Reset
Mozilla Firefox
- Open Mozilla and press Alt+H
- Choose Troubleshooting Information
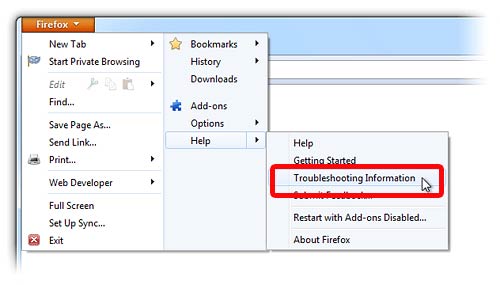
- Click Reset Firefox and confirm your action
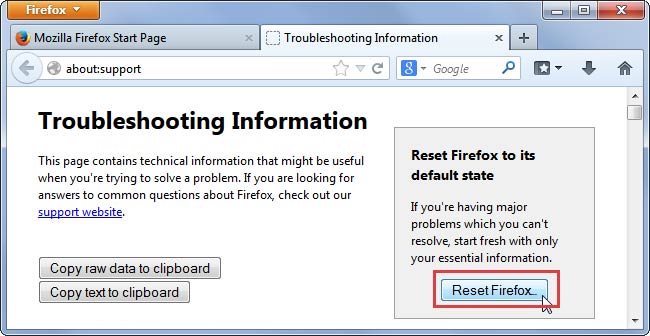
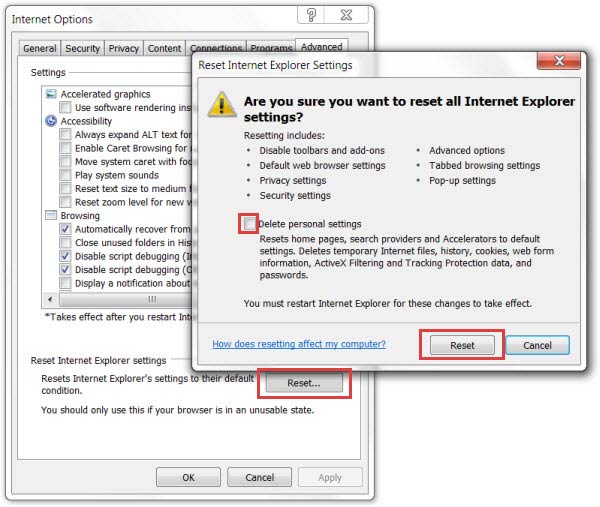
Internet Explorer
- Open IE and press Alt+T
- Click on Internet Options
- Go to the Advanced tab and click Reset
- Enable Delete personal settings and click Reset